IT Asset Disposition: Completing the Information Lifecycle
 Companies are constantly at risk for a data breach, disaster scenarios, hacks, outages and a variety of other threats that put their information in danger. It’s important that corporations have strategies in place and solutions that can handle the variety of potential fallouts a negative file scenario can dole out, especially when it comes to handling IT asset disposition. While many businesses may focus on the start of a file’s lifecycle in the corporate environment, it’s equally vital that professionals are aware of when and how to expire these resources securely.
Companies are constantly at risk for a data breach, disaster scenarios, hacks, outages and a variety of other threats that put their information in danger. It’s important that corporations have strategies in place and solutions that can handle the variety of potential fallouts a negative file scenario can dole out, especially when it comes to handling IT asset disposition. While many businesses may focus on the start of a file’s lifecycle in the corporate environment, it’s equally vital that professionals are aware of when and how to expire these resources securely.
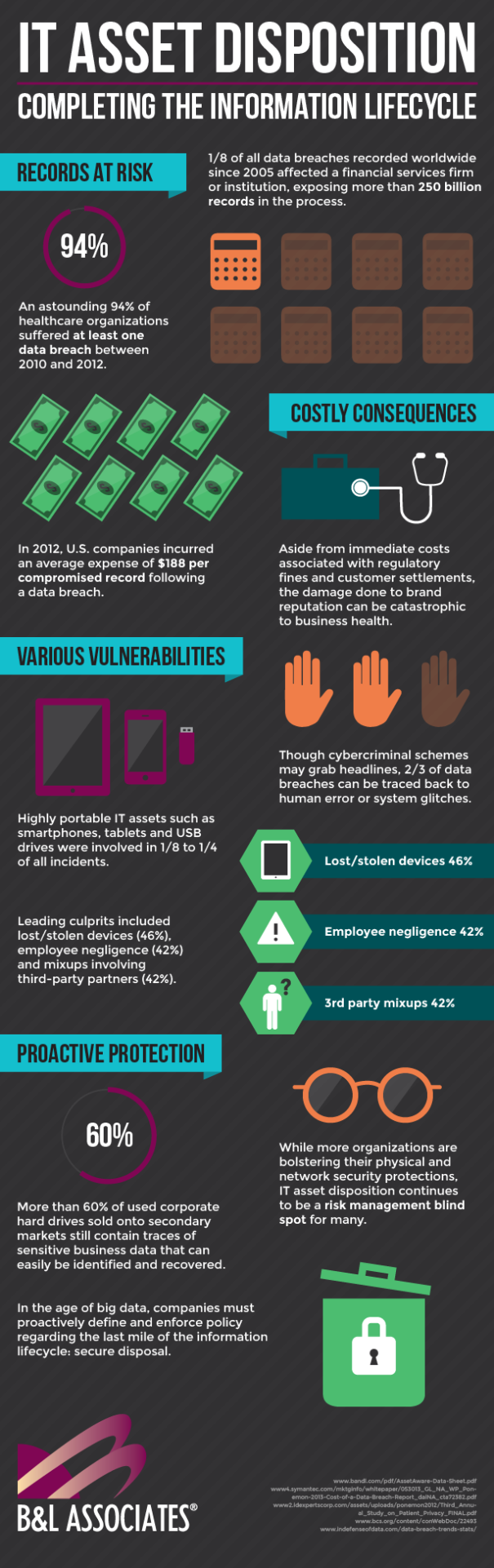
The variety of threats that impact IT asset disposition are on the rise as companies increase their connectivity options. There are various paths such as destruction or re purposing, multiple people or locations involved, the need to be able to verify all assets were destroyed, etc. Software can help manage these processes in order to keep data secure, but only if corporations are actively engaging with these kinds of technological tools. The trouble is, with 94 percent of organizations suffering some kind of data breach in the last three years, it’s important that businesses start taking a closer look at where their leaks are coming from.
Currently, businesses are looking at loss from two main points: physical loss and online incursions. These two arenas have shown considerable increases in veracity in recent years due to enhancing portability and availability of business infrastructure. Whether it’s the presence of cloud-deployed Software-as-a-Service or the carrying capacity of mobile devices to access corporate data portals, the availability of these resources makes it easy for firms to lose their most valuable assets.
One of the biggest considerations organizations should take into account is the volatility of hardware in the enterprise landscape. This pertains to personal portable devices like smartphones and laptops as well as hard disk management tools. Carrying out accurate and thorough IT asset disposition requires that businesses pay attention to the entire lifecycle corporate hardware, including the matter of wiping and destroying old devices. At present, about 60 percent of all corporations currently have issues with ensuring that their hard disk drives sold to resellers and other outlets aren’t properly wiped. It’s important that companies take these factors into account when trying to handle their hardware security.
What’s more, corporations should be aware that they face ever-increasing financial and public repercussions for failing to properly protect their assets. The simple act of incurring an outage or data breach causes companies to suffer significant disaster fallout and catastrophic corporate problems, so taking these kinds of scenarios into account demands that organizations keep up with modern trends in IT asset disposition.
